
1 基础知识
1.1 ACME
– ACME即英文Automatic Certificate Management Environment的英文缩写
– ACME是一种通讯协议,用于自动证书颁发机构与用户服务器之间的自动证书部署
– ACME协议基于HTTPS传递JSON格式的消息
1.2 Let’s Encrypt证书管理软件
1.2.1 工作原理
– 管理软件向证书颁发机构证明该服务器拥有域名控制权
– 管理软件向证书颁发机构申请、续期或吊销该域名证书
1.2.2 域名认证
– Let’s Encrypt通过公钥识别服务器管理员
– 证书管理软件首次与Let’s Encrypt交互时,会生成新的密钥对
– 证书管理软件会向Let’s Encrypt CA证明服务器控制着一个或多个域名(域名认证或URL认证)
关于域名认证方式,有两种方法
DNS认证,以“example.com”为例,创建Let’s Encrypt指定的CNAME即可完成认证
URL认证,以“example.com”为例,创建Let’s Encrypt指定的URL即可完成认证
一次数字密码,
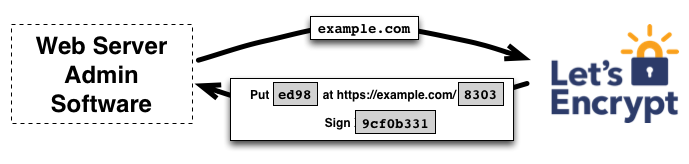
如上图所示,
– Let’s Encrypt返回一个一次性密码到管理软件
– 管理软件需要用对一次性使用私钥签名以证明秘钥属于管理软件
以下是驾驶使用URL认证并配合一次性密码的交互过程,
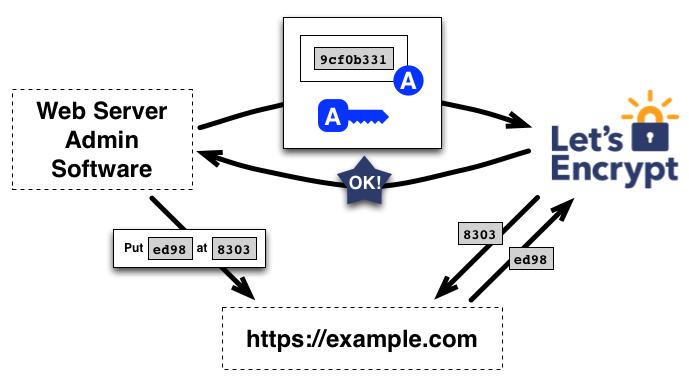
1.2.3 证书的颁发与吊销
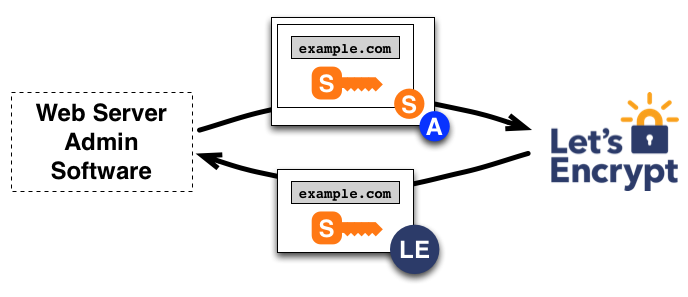
如上图所示,
– 证书管理软件创建一个PKCS#10(证书签名请求CSR)请求Let’s Encrypt CA为指定公钥颁发证书
– CSR由管理软件使用私钥进行一次签名,然后再用授权秘钥对整个CSR进行一次签名,以便Let’s Encrypt CA验证其来源
– Let’s Encrypt CA收到请求后对两份签名进行验证,如果全部通过则为CSR中的公钥颁发证书并返回证书到管理软件
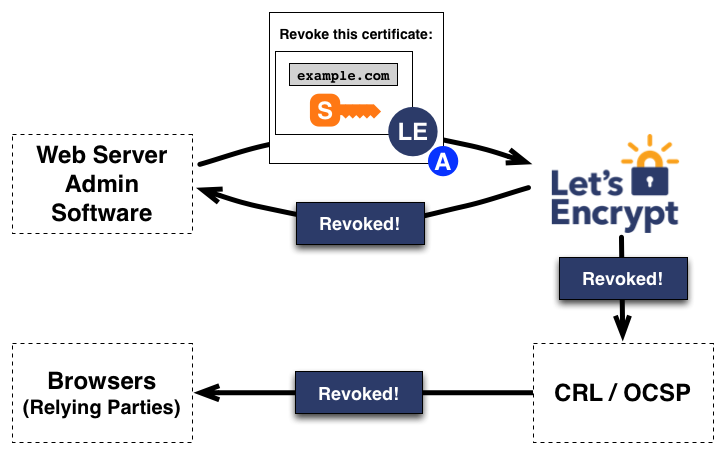
如上图所示,
– 证书管理软件授权私钥签署一个吊销证书请求用于Let’s Encrypt验证该请求是否已被授权
– 如已授权,则将吊销信息发布到正常的吊销通道(OCSP)中通知浏览器等依赖放他们不再信任该证书
2 最佳实践
2.1 安装Snapd包管理工具
2.2 安装Certbot
2.2.1 安装软件包
snap install --classic certbot
2.2.2 配置软链接
ln -s /snap/bin/certbot /usr/bin/certbot
2.2.3 获取帮助手册
certbot --help
可见如下输出,
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
certbot [SUBCOMMAND] [options] [-d DOMAIN] [-d DOMAIN] ...
Certbot can obtain and install HTTPS/TLS/SSL certificates. By default,
it will attempt to use a webserver both for obtaining and installing the
certificate. The most common SUBCOMMANDS and flags are:
obtain, install, and renew certificates:
(default) run Obtain & install a certificate in your current webserver
certonly Obtain or renew a certificate, but do not install it
renew Renew all previously obtained certificates that are near
expiry
enhance Add security enhancements to your existing configuration
-d DOMAINS Comma-separated list of domains to obtain a certificate for
--apache Use the Apache plugin for authentication & installation
--standalone Run a standalone webserver for authentication
--nginx Use the Nginx plugin for authentication & installation
--webroot Place files in a server's webroot folder for authentication
--manual Obtain certificates interactively, or using shell script
hooks
-n Run non-interactively
--test-cert Obtain a test certificate from a staging server
--dry-run Test "renew" or "certonly" without saving any certificates
to disk
manage certificates:
certificates Display information about certificates you have from Certbot
revoke Revoke a certificate (supply --cert-name or --cert-path)
delete Delete a certificate (supply --cert-name)
reconfigure Update a certificate's configuration (supply --cert-name)
manage your account:
register Create an ACME account
unregister Deactivate an ACME account
update_account Update an ACME account
show_account Display account details
--agree-tos Agree to the ACME server's Subscriber Agreement
-m EMAIL Email address for important account notifications
More detailed help:
-h, --help [TOPIC] print this message, or detailed help on a topic;
the available TOPICS are:
all, automation, commands, paths, security, testing, or any of the
subcommands or plugins (certonly, renew, install, register, nginx,
apache, standalone, webroot, etc.)
-h all print a detailed help page including all topics
--version print the version number
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
2.3 证书操作
2.3.1 仅获取证书
certbot certonly --nginx
向导如下,
Saving debug log to /var/log/letsencrypt/letsencrypt.log Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): will@cmdschool.org - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.3-September-21-2022.pdf. You must agree in order to register with the ACME server. Do you agree? - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: Y - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Would you be willing, once your first certificate is successfully issued, to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: Y Account registered. Which names would you like to activate HTTPS for? We recommend selecting either all domains, or all domains in a VirtualHost/server block. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - 1: cmdschool.org 2: www.cmdschool.org 3: www.cmdschool.net 4: www.cmdschool.com 5: www.cmdschool.cn - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Select the appropriate numbers separated by commas and/or spaces, or leave input blank to select all options shown (Enter 'c' to cancel): 2,3,4,5 Requesting a certificate for www.cmdschool.org and 3 more domains Successfully received certificate. Certificate is saved at: /etc/letsencrypt/live/www.cmdschool.org/fullchain.pem Key is saved at: /etc/letsencrypt/live/www.cmdschool.org/privkey.pem This certificate expires on 2023-09-28. These files will be updated when the certificate renews. Certbot has set up a scheduled task to automatically renew this certificate in the background. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - If you like Certbot, please consider supporting our work by: * Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate * Donating to EFF: https://eff.org/donate-le - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
2.3.2 查询获取到的证书
certbot certificates
可见如下输出,
Saving debug log to /var/log/letsencrypt/letsencrypt.log
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Found the following certs:
Certificate Name: www.cmdschool.org
Serial Number: 447e7ec9a6cc09f160b5ed91bd2d22ae84b
Key Type: ECDSA
Domains: www.cmdschool.org www.cmdschool.cn www.cmdschool.com www.cmdschool.net
Expiry Date: 2023-09-28 06:52:05+00:00 (VALID: 89 days)
Certificate Path: /etc/letsencrypt/live/www.cmdschool.org/fullchain.pem
Private Key Path: /etc/letsencrypt/live/www.cmdschool.org/privkey.pem
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
2.3.3 配置Nginx加载证书
vim /etc/nginx/conf.d/www.cmdschool.org_443.conf
加入如下配置,
server {
#...
ssl_certificate /etc/letsencrypt/live/www.cmdschool.org/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/www.cmdschool.org/privkey.pem;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers on;
ssl_ciphers ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
#...
}
2.3.4 配置自动续订
crontab -e
加入如下配置,
0 6 * * * /usr/bin/certbot renew --quiet
需要注意的是,
– 命令行每天6点0分触发一次命令行
– 命令行检查证书是否在30天内过期,符合条件则自动更新
– 已安装的证书将自动更新并重新加载
参阅文档
======================
Let’s Encrypt的工作原理
————————
https://letsencrypt.org/zh-cn/how-it-works/
ACME协议
—————–
https://en.wikipedia.org/wiki/Automatic_Certificate_Management_Environment
https://datatracker.ietf.org/doc/html/rfc8555
ACME客户端
————-
https://letsencrypt.org/zh-cn/docs/client-options/
nginx的配置范例
——————
https://www.nginx.com/blog/using-free-ssltls-certificates-from-lets-encrypt-with-nginx/
没有评论