您好,我想麻烦下您,您能把每一个节Node的IP详细说明一下麽?第一个IP:10.168.0.154我都没看明白 谢谢
如何实现samba4的负载均衡群集?
- By : Will
- Category : Load balancing, Samba
- Tags: LB, Load balancing, samba, samba4

1 架构简介
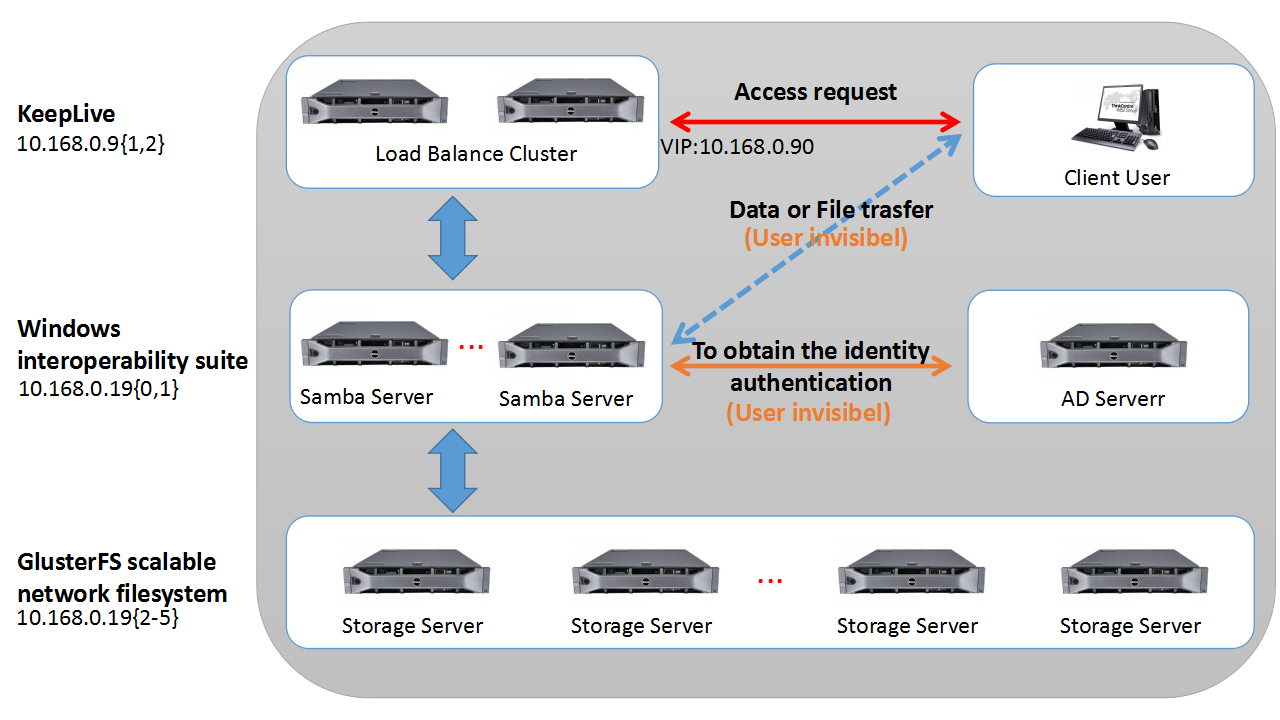
1.1 负载均衡器层
此层提供负载均衡的调度服务,把负载分派到各个文件系统服务器。
1.2 文件系统服务层
此层提供文件系统的存储、身份认证、权限控制等服务等,由基于Linux系统的Samba实现,结合AD提供的身份认证服务,可以提供与Windows一样的共享服务。
1.3 可扩展分布式存储层
此层为第一层提供可无限扩展的数据存取服务、Quota,由基于linux的GlusterFS群集实现,一共有4个节点。
1.4 集群工作流程分析
1)连接建立过程
step1 客户端访问负载均衡器的虚拟IP(10.10.2.90)
step2 负载均衡器检测到客户端访问请求的是虚拟IP的目标端口445/tcp或139/tcp
step3 负载均衡器将虚拟IP的MAC地址改为连接数最小的samba服务器MAC地址(ARP的解析过程)
step4 用户与连接数最小的samba服务器建立连接
2)数据上传过程
step1 用户上传文件到samba服务器且被samba服务器缓存在本地
step2 samba服务器将转存数据保存到后端存储层
3)数据读取过程
step1 用户到samba服务器取数据
step2 samba服务器从后端存储层将数据取出后再传送给用户
2 负载均衡器层
2.1 项目的简介
官方地址:
http://www.keepalived.org/

Keepalived的作用是检测服务器的状态,如果有一台文件服务器死机,或工作出现故障,Keepalived将检测到,并将有故障的服务器从系统中剔除,当服务器工作正常后Keepalived自动将服务器加入到服务器群中,这些工作全部自动完成,不需要人工干涉,需要人工做的只是修复故障的服务器。
2.2 工作原理
2.2.1 LVS的架构
1)调度层(Director):
2)集群层(Real Server)
3)共享层
2.2.2 LVS的三种工作模式
1)DR模式
– MAC层实现
– Director将请求的数据包目标MAC改为Real Server的MAC地址
– 数据直接返回客户端
2)NAT模式
– IP层实现
– Director将请求的目标IP改为Real Server的IP
– 数据返回在Director将源IP还原
3)TUN模式
– 类似于VPN实现
– Director建立加密IP隧道转发到Real Server
– 数据直接返回客户端
2.2.3 LVS的IP分类
1)VIP(Virtual IP)
– VIP每台机都需要配置
– IP用于内网通讯并对外提供服务
2)DIP(Driector IP)
– DIP设置于Driector服务器
– 分内外网IP,内网IP用于内部通讯,外网IP用于NAT模式的外网
3)RIP(Real IP)
– RIP设置于Real服务器
– 只有内网IP,IP只用于内网通讯
2.2.4 LVS的调度算法
1)轮叫调度(Round Robin,简称RR)
2)加权轮叫(Weighted Round Robin,简称WRR)
3)最少链接(Least Connection,简称LC)
4)加权最少链接(Weighted Least Conncetions,简称WLC)
2.3 Keeplived的配置
2.3.1 环境配置
KeepLive{1-2}
hostname=Keeplive{1-2}.cmdschool.org
ipaddress=10.168.0.9{0-1}
OS=CentOS 6.8
2.3.2 配置NTP
In KeepLive{1-2} :
1)安装ntp的相关包
yum install -y chrony
2)指定内网的NTP服务器
vim /etc/chrony.conf
更改如下配置:
#server 0.rhel.pool.ntp.org iburst #server 1.rhel.pool.ntp.org iburst #server 2.rhel.pool.ntp.org iburst #server 3.rhel.pool.ntp.org iburst server 10.168.0.154 iburst
3)启动服务并配置开机自启动
/etc/init.d/chronyd start chkconfig chronyd on
4)同步时间
chronyc sources
2.3.3 配置Keepalived服务
1)软件包安装
In KeepLive{1-2} :
yum install -y ipvsadm keepalived
2)配置主服务器
In KeepLive{1-2} :
cp /etc/keepalived/keepalived.conf /etc/keepalived/keepalived.conf.default echo "" > /etc/keepalived/keepalived.conf vim /etc/keepalived/keepalived.conf
配置如下:
In KeepLive1 :
vrrp_instance VI_1 {
state MASTER #备用服务器上为 BACKUP
interface eth0
virtual_router_id 51
priority 100 #备用服务器上为90
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
10.168.0.90
}
}
virtual_server 10.168.0.90 445 {
delay_loop 6 #(每隔6秒查询realserver状态)
lb_algo wlc #(lvs 算法)
lb_kind DR #(Direct Route)
persistence_timeout 7200 #(同一IP的连接7200秒内被分配到同一台realserver)
protocol TCP #(用TCP协议检查realserver状态)
real_server 10.168.0.190 445 {
weight 100 #(权重)
TCP_CHECK {
connect_timeout 10 #(10秒无响应超时)
nb_get_retry 3
delay_before_retry 3
connect_port 445
}
}
real_server 10.168.0.191 445 {
weight 100
TCP_CHECK {
connect_timeout 10
nb_get_retry 3
delay_before_retry 3
connect_port 445
}
}
}
virtual_server 10.168.0.90 139 {
delay_loop 6 #(每隔6秒查询realserver状态)
lb_algo wlc #(lvs 算法)
lb_kind DR #(Direct Route)
persistence_timeout 7200 #(同一IP的连接7200秒内被分配到同一台realserver)
protocol TCP #(用TCP协议检查realserver状态)
real_server 10.168.0.190 139 {
weight 100 #(权重)
TCP_CHECK {
connect_timeout 10 #(10秒无响应超时)
nb_get_retry 3
delay_before_retry 3
connect_port 139
}
}
real_server 10.168.0.190 139 {
weight 100
TCP_CHECK {
connect_timeout 10
nb_get_retry 3
delay_before_retry 3
connect_port 139
}
}
}
In KeepLive2 :
vrrp_instance VI_1 {
state BACKUP #主服务器上为 MASTER
interface eth0
virtual_router_id 51
priority 90 #主服务器上为100
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
10.168.0.90
}
}
virtual_server 110.168.0.90 445 {
delay_loop 6 #(每隔6秒查询realserver状态)
lb_algo wlc #(lvs 算法)
lb_kind DR #(Direct Route)
persistence_timeout 7200 #(同一IP的连接7200秒内被分配到同一台realserver)
protocol TCP #(用TCP协议检查realserver状态)
real_server 10.168.0.190 445 {
weight 100 #(权重)
TCP_CHECK {
connect_timeout 10 #(10秒无响应超时)
nb_get_retry 3
delay_before_retry 3
connect_port 445
}
}
real_server 10.168.0.191 445 {
weight 100
TCP_CHECK {
connect_timeout 10
nb_get_retry 3
delay_before_retry 3
connect_port 445
}
}
}
virtual_server 10.168.0.90 139 {
delay_loop 6 #(每隔6秒查询realserver状态)
lb_algo wlc #(lvs 算法)
lb_kind DR #(Direct Route)
persistence_timeout 7200 #(同一IP的连接7200秒内被分配到同一台realserver)
protocol TCP #(用TCP协议检查realserver状态)
real_server 10.168.0.190 139 {
weight 100 #(权重)
TCP_CHECK {
connect_timeout 10 #(10秒无响应超时)
nb_get_retry 3
delay_before_retry 3
connect_port 139
}
}
real_server 10.168.0.191 139 {
weight 100
TCP_CHECK {
connect_timeout 10
nb_get_retry 3
delay_before_retry 3
connect_port 139
}
}
}
3)启动服务并配置开机启动
In KeepLive{1-2} :
/etc/init.d/keepalived start chkconfig keepalived on
2.3.4 配置路由转发
In KeepLive{1-2} :
1)临时开启路由转发
echo 1 > /proc/sys/net/ipv4/ip_forward
2)永久开启路由转发
vim /etc/sysctl.conf
修改如下配置
net.ipv4.ip_forward = 1
2.3.5 配置防火墙
In KeepLive{1-2} :
vim /etc/sysconfig/iptables
加入如下条目:
-A INPUT -m state --state NEW -m tcp -p tcp --dport 139 -j ACCEPT -A INPUT -m state --state NEW -m tcp -p tcp --dport 445 -j ACCEPT
重启防火墙使配置生效
/etc/init.d/iptables restart
2.3.6 配置Real Server服务器
In GlusterGW0{1-2} :
1)编辑配置脚本
vim /usr/local/sbin/lvs_dr_rs.sh
输入如下内容:
#! /bin/bash vip=10.168.0.90 ifconfig lo:0 $vip broadcast $vip netmask 255.255.255.255 up route add -host $vip lo:0 echo "1" >/proc/sys/net/ipv4/conf/lo/arp_ignore echo "2" >/proc/sys/net/ipv4/conf/lo/arp_announce echo "1" >/proc/sys/net/ipv4/conf/all/arp_ignore echo "2" >/proc/sys/net/ipv4/conf/all/arp_announce
2)执行配置脚本
sh /usr/local/sbin/lvs_dr_rs.sh echo 'sh /usr/local/sbin/lvs_dr_rs.sh' >> /etc/rc.local
3 文件系统服务层
3.1 理论基础
3.1.1 samba的简介
https://www.samba.org

Samba是在Linux和UNIX系统上实现SMB协议的一个免费软件,由服务器及客户端程序构成。SMB(Server Messages Block,信息服务块)是一种在局域网上共享文件和打印机的一种通信协议,它为局域网内的不同计算机之间提供文件及打印机等资源的共享服务。SMB协议是客户机/服务器型协议,客户机通过该协议可以访问服务器上的共享文件系统、打印机及其他资源。通过设置“NetBIOS over TCP/IP”使得Samba不但能与局域网络主机分享资源,还能与全世界的电脑分享资源。
3.1.2 samba的起源
1991 年一个名叫Andrew Tridgwell 的大学生就有这样的困扰,他手上有三部机器,分别是跑DOS 的个人计算机、DEC公司的 Digital Unix 系统以及 Sun 的 Unix 系统。在当时,DEC 公司有发展出一套称为 PATHWORKS 的软件,这套软件可以用来分享 DEC 的Unix 与个人计算机的 DOS 这两个操作系统的档案数据,可惜让 Tridgwell 觉得较困扰的是,Sun的 Unix 无法藉由这个软件来达到数据分享的目的。这个时候 Tridgwell 就想说:『咦!既然这两部系统可以相互沟通,没道理Sun 就必需这么苦命吧?可不可以将这两部系统的运作原理找出来,然后让 Sun这部机器也能够分享档案数据呢?』,为了解决这样的的问题,这老兄就自行写了个program 去侦测当 DOS 与 DEC 的 Unix 系统在进行数据分享传送时所使用到的通讯协议信息,然后将这些重要的信息撷取下来,并且基于上述所找到的通讯协议而开发出ServerMessage Block (SMB) 这个档案系统,而就是这套 SMB软件能够让 Unix 与 DOS 互相的分享数据!( 注:再次的给他强调一次,在Unix Like 上面可以分享档案数据的 file system 是 NFS,那么在 Windows 上面使用的『网络邻居』所使用的档案系统则称为Common Internet File System, CIFS )
3.2 推荐配置
3.2.1 Windows Server 2008 R2 server
– Deploy Windows Server 2008 R2
– Configure Active Directory Domain Services
3.2.2 Red Hat Enterprise Linux 6 systems
– Deploy Red Hat Enterprise Linux 6
– Configure SELinux Security Parameters
– Install/Configure Samba (Recommended Configurations 1, 2 only)
– Synchronize Time Services
– Configure DNS
– Install/Configure Kerberos Client
– Install oddjob-mkhomedir
3.3 Winbind Backends的分类
| Backend | Type | ID Mappings | Advantages | Disadvantages |
| idmap_tdb | Read/Write | Allocating
(分配) |
Simplest to implement
简单实现 Default winbind backend 默认的winbind后端 |
Limited scalability – not intended for consistent ID mappings across multiple RHEL servers
有限的伸缩性 – 没有专为跨多个RHEL服务器提供一致的ID映射 Cache corruption requires manual intervention to correct file ownership 缓存损坏需要手动介入去修正文件所有权 Static – 1 tdb entry for each SID(slower) 静态 – 为每一个SID配置1个tdb条目 |
| idmap_rid | Read-only | Algorithmic
(算法) |
User algorithmic ID mappings across multiple servers(faster)
用户通过算法将ID映射到多个服务器(快) |
Requires additional configuration work to support a forest of AD domains or multiple domain trees
需要额外的配置工作去支持一个AD域的森林或多个域树 |
| idmap_ad | Read-only | Assigned by admin
(由管理员指定) |
Standardized user configuration (shell,home directory)
标准用户配置(shell,家目录) Centralized user account managenment 集中式用户账号管理 |
Requires additional configuration work to support a forest of AD domains or multiple domain trees
需要额外的配置工作去支持一个AD域的森林或多个域树 Requires additional user management tasks – user/group ID attributes mustbe specified within AD 需要额外的用户管理任务 – 用户/组ID属性必须在AD内指定 |
| idmap_ldap | Read/Write | Allocating
(分配) |
ID mappings stored in centralized,non-AD server(RHDS,OpenLDAP,etc.)
ID映射集中存储在非AD服务器(RHDS,OpenLDAP,etc.) |
Requires external LDAP server
需要外部的LDAP服务器 Most complex configuration to implement due to Samba LDAP mapping limitations(UID/GID not store at POSIX level) 最复杂的配置去实现Samba的LDAP映射限制(UID/GID不存储在POSIX级别) |
| idmap_adex | Read-only | Assigned by admin
(由管理员指定) |
Supports ID mappings using RFC2307 attributes
支持使用RFC2307属性进行ID映射 |
Not recommended for new deplyments(deprecated by latest versions of Samba)
不推荐用于新的部署(Samba最新版不推荐使用) |
| idmap_hash | Read-only | Algorithmic
(算法) |
Similar to idmap_rid but generates UID/GID from full domain SID
类似idmap_rid但是从全域SID生成UID/GID Mappings consistent across RHEL systems 跨越RHEL系统的映射一致 |
No additional configuration but potential risk of ID collisions
没有额外的配置但存在ID冲突的风险 |
| idmap_tdb2 | Read/Write | Allocating
(分配) |
Script option availabel for performing ID mappings via an external program
脚本选项可以通过一个外部程序执行ID映射 |
For Samba clusters(CTDB) only
仅适用于Samba群集 |
| idmap_nss | Read-only | Pre-existing
(预先存在的) |
Uses existing UID/GID mappings
使用一个已存在的UID/GID映射 |
No support for trusted domains
不支持信任域 Can’t resolve mappings unless SID is available 不能解决映射除非SID是可用的 |
3.4 winbind
3.4.1 winbind的数据库
ll /var/lib/samba/winbindd_*.tdb
显示如下:
-rw-------. 1 root root 32768 Aug 10 01:12 /var/lib/samba/winbindd_cache.tdb -rw-r--r--. 1 root root 421888 Aug 10 00:46 /var/lib/samba/winbindd_idmap.tdb
3.4.2 数据库的查看
1)安装工具
yum install -y tdb-tools
2)使用工具
tdbdump /var/lib/samba/winbindd_idmap.tdb tdbdump /var/lib/samba/winbindd_cache.tdb
3.5 环境配置
3.5.1 环境信息
ad1 server(信任dg.cmdschool.org):
hostname = rootad.cmdschool.org
ipaddress = 10.168.0.154
OS = window server 2008 R2
ad2 server(信任rootad.cmdschool.org):
hostname = dg.cmdschool.org
ipaddress = 10.168.0.155
OS = window server 2008 R2
samba server:
hostname = GlusterGW0{1-2}.cmdschoolo.org
ipaddress = 10.168.0.19{0-1}
OS = CentOS 6.8
3.5.2 部署Windows 2008 Server R2
详细请参阅:
https://technet.microsoft.com/en-us/library/dd283085.aspx
3.5.3 配置活动目录域服务
详细请参阅:
https://technet.microsoft.com/en-us/library/cc770946.aspx
3.5.4 配置分布式存储
由于samba本身并不支持群集,故此层是samba负载均衡成败的关键,故请务必注意:
1)扩展存储需要使用含Gluster 3.8及以上版本,
配置参阅:http://www.cmdschool.org/archives/92
2)分布式存储需要开启存储锁,
配置请参阅:http://www.cmdschool.org/archives/410
利用存储锁解决多台服务器之间Excel的独占编辑问题,防止多用户分布到不同的samba服务器同时编辑损坏文件。
3.6 基础配置
3.6.1 配置SElinux安全参数
In GlusterGW0{1-2} :
setenforce 0 sed -i 's/SELINUX=enforcing/SELINUX=disabled/g' /etc/selinux/config
3.6.2 名称解析配置
In GlusterGW0{1-2} :
1)hosts配置
echo "10.168.0.190 GlusterGW01.cmdschool.org GlusterGW01" >> /etc/hosts echo "10.168.0.191 GlusterGW02.cmdschool.org GlusterGW02" >> /etc/hosts echo "10.168.0.192 GlusterH01.cmdschool.org" >> /etc/hosts echo "10.168.0.193 GlusterH02.cmdschool.org" >> /etc/hosts echo "10.168.0.194 GlusterH03.cmdschool.org" >> /etc/hosts echo "10.168.0.195 GlusterH04.cmdschool.org" >> /etc/hosts
2)DNS服务器方式
echo "nameserver 10.168.0.154" >> /etc/resolv.conf echo "search ad.cmdschool.org" >> /etc/resolv.conf
3.6.3 域服务器验证
In GlusterGW0{1-2} :
1)安装DNS工具套件
yum install -y bind-utils
2)输入如下命令测试
host -t A ad.cmdschool.org
3.6.4 NTP配置
In GlusterGW0{1-2} :
1)rpm包的安装
yum install -y chrony
2)配置NTP服务器
vim /etc/chrony.conf
指定内网的NTP服务器,更改如下配置
#server 0.rhel.pool.ntp.org iburst #server 1.rhel.pool.ntp.org iburst #server 2.rhel.pool.ntp.org iburst #server 3.rhel.pool.ntp.org iburst server 10.168.0.154 iburst
3)启动服务
并配置开机自启动
/etc/init.d/chronyd start chkconfig chronyd on
4)同步时间
chronyc sources
3.6.5 配置yum源
In GlusterGW0{1-2} :
yum install -y https://dl.fedoraproject.org/pub/epel/epel-release-latest-6.noarch.rpm curl http://download.gluster.org/pub/gluster/glusterfs/3.7/LATEST/CentOS/glusterfs-epel.repo > /etc/yum.repos.d/glusterfs-epel.repo
3.6.6 配置防火墙
In GlusterGW0{1-2} :
/etc/init.d/iptables stop chkconfig iptables off
3.6.7 安装相关包
In GlusterGW0{1-2} :
1)安装相关包
yum -y install samba4 samba4-client samba4-common samba4-winbind samba4-winbind-clients
2)启动并校验服务
/etc/init.d/smb start /etc/init.d/smb status ps -aef | grep smb
3)配置服务开机自动启动
chkconfig smb on chkconfig --list smb
3.7 配置文件系统服务
3.7.1 配置Kerberos服务端
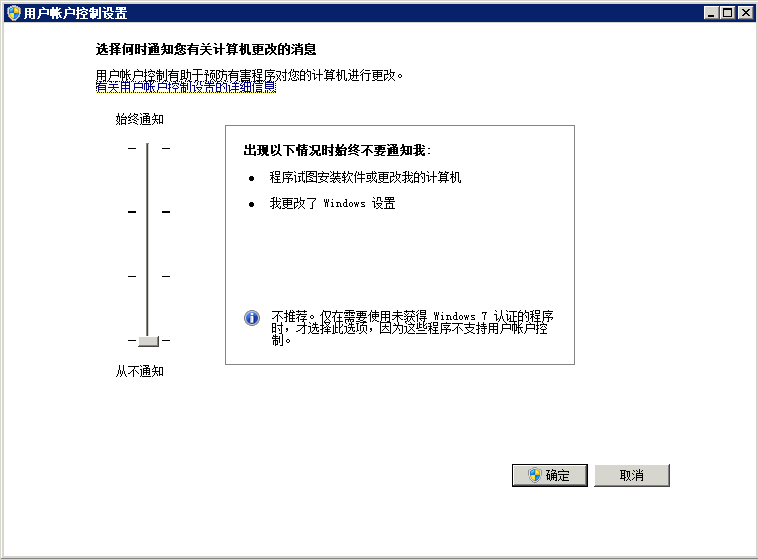
In AD Server :
1)关闭UAC并重启系统
2)新建认证用户
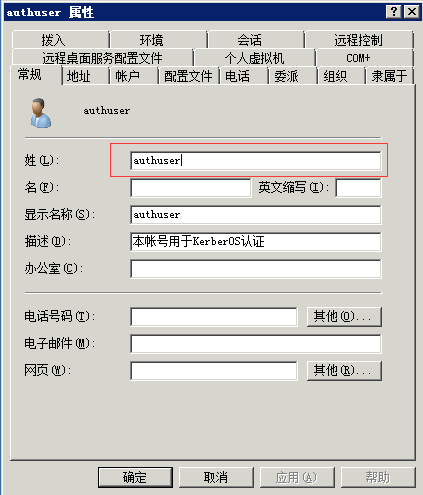
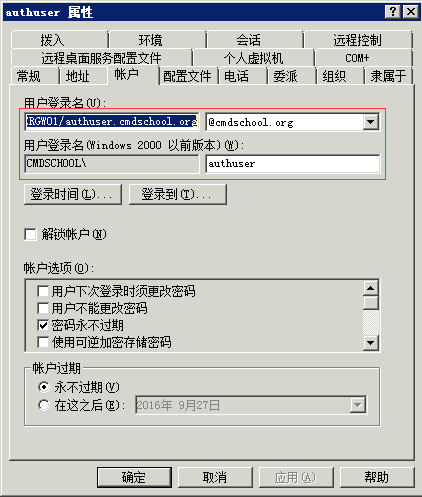
注:账号只需要一个即可实现多台服务器认证
3)生成证书到D盘根目录
命令行范例
setspn -A host/client.ad.example.com@AD.EXAMPLE.COM client setspn -L client ktpass /princ host/client.ad.example.com@AD.EXAMPLE.COM /out client-host.keytab /crypto all /ptype KRB5_NT_PRINCIPAL -desonly /mapuser AD\client$ +setupn +rndPass +setpass +answer
注:加证书只需要按照以上命令格式生成新的证书即可
实际操作
setspn -A GLUSTERGW02/authuser.cmdschool.org@CMDSCHOOL.ORG authuser setspn -L authuser ktpass /princ GLUSTERGW02/authuser.cmdschool.org@CMDSCHOOL.ORG /out authuser-GLUSTERGW02.keytab /crypto all /ptype KRB5_NT_PRINCIPAL -desonly /mapuser CMDSCHOOL\authuser +setupn +rndPass +setpass +answer setspn -A GLUSTERGW01/authuser.cmdschool.org@CMDSCHOOL.ORG authuser setspn -L authuser ktpass /princ GLUSTERGW01/authuser.cmdschool.org@CMDSCHOOL.ORG /out authuser-GLUSTERGW01.keytab /crypto all /ptype KRB5_NT_PRINCIPAL -desonly /mapuser CMDSCHOOL\authuser +setupn +rndPass +setpass +answer
3.7.2 配置Kerberos客户端
In GlusterGW0{1-2} :
1)证书安装
将Kerberos服务器端生成的证书分别复制到名称对应的客户端的/root目录下并执行以下命令:
cp authuser-GLUSTERGW*.keytab /etc/krb5.keytab chown root:root /etc/krb5.keytab chmod 0600 /etc/krb5.keytab restorecon /etc/krb5.keytab
2)安装Kerberos客户端rpm包
yum install -y krb5-workstation
3)编辑krb5配置文件
cp /etc/krb5.conf /etc/krb5.conf.default echo "" > /etc/krb5.conf vim /etc/krb5.conf
内容修改如下:
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
default_realm = CMDSCHOOL.ORG
dns_lookup_realm = false
dns_lookup_kdc = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
[realms]
CMDSCHOOL.ORG = {
kdc = rootad.cmdschool.org
admin_server = rootad.cmdschool.org
}
DG.CMDSCHOOL.ORG = {
kdc = dg.cmdschool.org:88
admin_server = dg.cmdschool.org:749
}
[domain_realm]
.cmdschool.org = ROOTAD.CMDSCHOOL.ORG
cmdschool.org = ROOTAD.CMDSCHOOL.ORG
.dg.cmdschool.org = DG.CMDSCHOOL.ORG
dg.cmdschool.org = DG.CMDSCHOOL.ORG
4)测试证书是否生效
kdestroy klist
可以看到如下提示:
klist: No credentials cache found (ticket cache FILE:/tmp/krb5cc_0)
5)初始化krb5
kinit administrator@CMDSCHOOL.ORG
确认是否成功
klist
成功可以看到如下信息:
Ticket cache: FILE:/tmp/krb5cc_0
Default principal: administrator@CMDSCHOOL.ORG
Valid starting Expires Service principal
08/28/16 08:59:12 08/28/16 18:59:17 krbtgt/CMDSCHOOL.ORG@CMDSCHOOL.ORG
renew until 09/04/16 08:59:12
3.7.3 加域并测试
1)增加加域信息
In GlusterGW0{1-2} :
cp /etc/samba/smb.conf /etc/samba/smb.conf.default echo "" > /etc/samba/smb.conf vim /etc/samba/smb.conf
修改如下信息:
[global]
workgroup = CMDSCHOOL
client signing = yes
client use spnego = yes
kerberos method = secrets and keytab
log file = /var/log/samba/%m.log
max log size = 50
password server = *
allow trusted domains = yes
realm = CMDSCHOOL.ORG
security = ads
idmap uid = 10000-19999
idmap gid = 10000-19999
idmap config CMDSCHOOL:backend = rid
idmap config CMDSCHOOL:range = 10000000-19999999
idmap config DG:backend = rid
idmap config DG:range = 20000000-29999999
winbind enum users = no
winbind enum groups = no
2)测试配置文件
In GlusterGW0{1-2} :
testparm
3)备份缓存信息
In GlusterGW0{1-2} :
/etc/init.d/smb stop /etc/init.d/winbind stop tar -cvf /var/tmp/samba-cache-backup.tar /var/lib/samba ls -l /var/tmp/samba-cache-backup.tar
4)清理缓存文件
In GlusterGW0{1-2} :
rm -f /var/lib/samba/*
4)确认清理
In GlusterGW0{1-2} :
kdestroy
正常显示如下或无输出:
kdestroy: No credentials cache found while destroying cache
运行
klist
正常显示如下:
klist: No credentials cache found (ticket cache FILE:/tmp/krb5cc_0)
5)成员服务为加域
In GlusterGW0{1-2} :
net ads join -U administrator
或者
net ads join -U administrator -S rootad.cmdschool.org
6)测试与域控的连接
In GlusterGW0{1-2} :
net ads testjoin
正常显示如下:
Join is OK
或
net ads info
显示如下:
LDAP server: 10.168.0.154 LDAP server name: RootAD.cmdschool.org Realm: CMDSCHOOL.ORG Bind Path: dc=CMDSCHOOL,dc=ORG LDAP port: 389 Server time: Sun, 28 Aug 2016 09:04:08 CST KDC server: 10.168.0.154 Server time offset: 0
7)配置密码认证
In GlusterGW0{1-2} :
vim /etc/nsswitch.conf
修改内容如下:
passwd: files winbind group: files winbind
8)初始化Kerberos连接
In GlusterGW0{1-2} :
kinit administrator@CMDSCHOOL.ORG
9)启动winbind服务并配置服务自动启动
In Samba{1-2} :
/etc/init.d/winbind start chkconfig winbind on
10)测试
In GlusterGW0{1-2} :
获取用户:
wbinfo -u wbinfo -u --domain DG.CMDSCHOOL.ORG
显示如下:
CMDSCHOOL\administrator CMDSCHOOL\guest CMDSCHOOL\krbtgt CMDSCHOOL\user1 CMDSCHOOL\user2 CMDSCHOOL\user3 CMDSCHOOL\authuser CMDSCHOOL\dg$ DG\administrator DG\guest DG\krbtgt DG\cmdschool$
获取组信息:
wbinfo -g wbinfo -g --domain DG.CMDSCHOOL.ORG
显示如下:
CMDSCHOOL\domain computers CMDSCHOOL\domain controllers CMDSCHOOL\schema admins CMDSCHOOL\enterprise admins CMDSCHOOL\cert publishers CMDSCHOOL\domain admins CMDSCHOOL\domain users CMDSCHOOL\domain guests CMDSCHOOL\group policy creator owners CMDSCHOOL\ras and ias servers CMDSCHOOL\allowed rodc password replication group CMDSCHOOL\denied rodc password replication group CMDSCHOOL\read-only domain controllers CMDSCHOOL\enterprise read-only domain controllers CMDSCHOOL\dnsadmins CMDSCHOOL\dnsupdateproxy CMDSCHOOL\gp1 CMDSCHOOL\gp2 CMDSCHOOL\gps DG\domain computers DG\domain controllers DG\domain admins DG\domain users DG\domain guests DG\group policy creator owners DG\read-only domain controllers DG\dnsupdateproxy
11)单用户身份测试
id "CMDSCHOOL\administrator" id "DG\administrator"
显示如下:
uid=10000500(CMDSCHOOL\administrator) gid=10000513(CMDSCHOOL\domain users) groups=10000513(CMDSCHOOL\domain users),10000500(CMDSCHOOL\administrator),10000572(CMDSCHOOL\denied rodc password replication group),10000518(CMDSCHOOL\schema admins),10000519(CMDSCHOOL\enterprise admins),10000512(CMDSCHOOL\domain admins),10000520(CMDSCHOOL\group policy creator owners) uid=20000500(DG\administrator) gid=20000513(DG\domain users) groups=20000513(DG\domain users),20000500(DG\administrator),20000572(DG\denied rodc password replication group),20000512(DG\domain admins),20000520(DG\group policy creator owners)
12)显示所有域
wbinfo --all-domains
显示如下:
BUILTIN GLUSTERGW01 CMDSCHOOL DG
13)启动samba服务
In GlusterGW0{1-2} :
/etc/init.d/smb start
3.7.4 挂载共享存储
1)安装客户端yum包
In GlusterGW0{1-2} :
yum install -y glusterfs-fuse
2)手动挂载测试
In GlusterGW0{1-2} :
mount -t glusterfs GlusterH01.cmdschool.org:/gv0 /mnt mount umount /mnt
3)自动挂载测试
In GlusterGW0{1-2} :
mkdir /data
编辑挂载点:
In GlusterGW01 :
echo 'GlusterH01.cmdschool.org:/gv0 /data glusterfs defaults,acl 0 0' >> /etc/fstab
In GlusterGW02 :
echo 'GlusterH02.cmdschool.org:/gv0 /data glusterfs defaults,acl 0 0' >> /etc/fstab
4)尝试挂载
In GlusterGW0{1-2} :
mount -a & mount
5)检查挂载
In GlusterGW0{1-2} :
df -h
显示如下:
Filesystem Size Used Avail Use% Mounted on
/dev/mapper/VG_OS-lv_root
18G 912M 16G 6% /
tmpfs 1.5G 0 1.5G 0% /dev/shm
/dev/sda1 488M 37M 426M 8% /boot
GlusterH01.cmdschool.org:/gv0
400G 5.0G 395G 2% /data
3.7.5 配置根据组授权的共享
目标:实现根据组授权的共享
优点:用户可以通过微软的ADMINPACK工具简单地修改组成员授予用户读写权限
缺点:用户无法自定修改文件的ACL授权
1)创建用户目录
In GlusterGW01 :
mkdir -p /data/share{1,2}
2)目录授权
In GlusterGW01 :
chmod 777 /data/share1 chmod 777 /data/share2
3)创建samba配置目录
In GlusterGW01 :
mkdir -p /data/samba.d/
注:本目录用于存储samba的配置文件,所有samba服务器到此加载共享配置,需严格备份此文件夹的配置
4)修改配置文件
In GlusterGW01 :
vim /data/samba.d/share1.smb.conf
加入如下配置:
[share1]
path = /data/share1
valid users = "@CMDSCHOOL\gp1"
write list = "@CMDSCHOOL\gp1"
create mask = 666
directory mask = 777
注:以上share1授权给gp1组(具有读写权限)
In GlusterGW01 :
vim /data/samba.d/share2.smb.conf
加入如下配置:
[share2]
path = /data/share2
valid users = "@CMDSCHOOL\gp2"
write list = "@CMDSCHOOL\gp2"
create mask = 666
directory mask = 777
注: 以上share2授权给gp2组(具有读写权限)
4)引入配置samba配置
In GlusterGW0{1-2} :
echo "include = /data/samba.d/share1.smb.conf" >> /etc/samba/smb.conf echo "include = /data/samba.d/share2.smb.conf" >> /etc/samba/smb.conf
注:如果你想隐藏其他的共享,只显示当前加载的共享请使用如下配置
echo "config file = /data/samba.d/share1.smb.conf" >> /etc/samba/smb.conf echo "config file = /data/samba.d/share2.smb.conf" >> /etc/samba/smb.conf
重启服务:
/etc/init.d/smb restart
3.7.6 配置文件ACL控制的共享
目标:实现根据文件ACL授权的共享
优点:用户可以通过编辑文件的ACL来定义员授予用户读写权限
缺点:由于权限是用户定义,管理上会增加运维人员工作量
1)创建用户目录
In GlusterGW01 :
mkdir -p /data/share3
2)目录授权
chmod 700 /data/share3
3)指定目录的管理员
In GlusterGW01 :
chown "CMDSCHOOL\user3": /data/share3/
4)修改配置文件
In GlusterGW01 :
vim /data/samba.d/share3.smb.conf
加入如下配置:
[share3]
path = /data/share3
valid users = "@CMDSCHOOL\domain users"
write list = "@CMDSCHOOL\domain users"
create mask = 660
directory mask = 770
5)引入配置samba配置并使配置生效
In GlusterGW0{1-2} :
echo "include = /data/samba.d/share3.smb.conf" >> /etc/samba/smb.conf /etc/init.d/smb restart
6)管理员成员授权
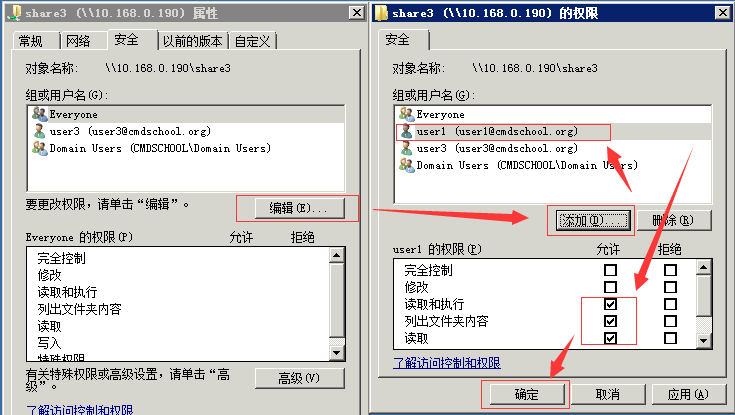
注:
1)亦可授权给组,根据具体情况定义
2)如果不支持,请参阅3.2.16的配置
从Linux系统底层可发现是通过文件的ACL实现的
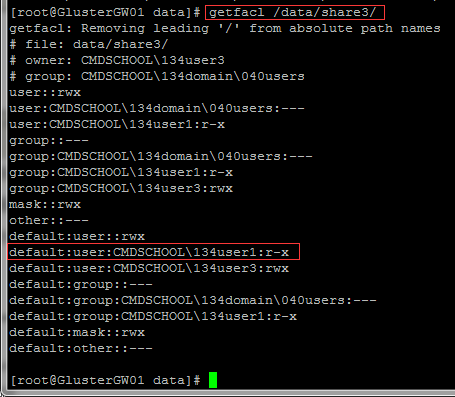
3.7.7 配置用户私有的共享
目标:使用用户触发式自动配置满足用户私有目录的需求
1)创建脚本存放目录
In GlusterGW01 :
mkdir -p /data/samba.d/scripts
注:本目录用于存储samba的配置脚本文件,所有samba服务器到此加载,需严格备份此文件夹的配置
2)创建用户目录配置脚本
In GlusterGW01 :
vim /data/samba.d/scripts/domain_add_user.sh
输入如下内容
#!/bin/bash domain=$1 user=$2 rootdir="/data/$domain" homedir="/data/$domain/$user" if [ ! -d "$rootdir" ]; then /bin/mkdir -p "$rootdir" /bin/chmod 777 "$rootdir" fi if [ ! -d "$homedir" ]; then /bin/mkdir -p "$homedir" /bin/chown "$domain\\$user": "$homedir" /bin/chmod 700 "$homedir" fi
3)授予脚本执行权限
In GlusterGW01 :
chmod 755 /data/samba.d/scripts/domain_add_user.sh
4)测试脚本
In GlusterGW01 :
/data/samba.d/scripts/domain_add_user.sh CMDSCHOOL user1 ls -l /data/
显示效果如下:
total 20 drwxrwxrwx 3 root root 4096 Aug 28 2016 CMDSCHOOL drwxr-xr-x 3 root root 4096 Aug 28 2016 samba.d drwxrwxrwx 2 root root 4096 Aug 28 2016 share1 drwxrwxrwx 2 root root 4096 Aug 28 2016 share2 drwxrwx---+ 2 CMDSCHOOL\user3 CMDSCHOOL\domain users 4096 Aug 28 2016 share3
清理用户文件夹:
rm -rf /data/CMDSCHOOL/*
注:由于“/data”目录下的文件夹只能由“root”用户创建,故不能删除“/data/CMDSCHOOL”文件夹
5)创建samba配置文件
In GlusterGW01 :
vim /data/samba.d/homes.smb.conf
测试脚本
[homes]
comment = Home Directories
browseable = no
valid users = "@CMDSCHOOL\gp2","@CMDSCHOOL\gp1"
write list = "@CMDSCHOOL\gp2","@CMDSCHOOL\gp1"
path = "/data/%D/%U"
create mask = 600
directory mask = 700
preexec = /data/samba.d/scripts/domain_add_user.sh %D %U
[%D]
valid users = "@CMDSCHOOL\gp2","@CMDSCHOOL\gp1"
write list = "@CMDSCHOOL\gp2","@CMDSCHOOL\gp1"
path = "/data/%D"
create mask = 600
directory mask = 700
preexec = /data/samba.d/scripts/domain_add_user.sh %D %U
6)引入配置samba配置并使配置生效
In GlusterGW0{1-2} :
echo "include = /data/samba.d/homes.smb.conf" >> /etc/samba/smb.conf /etc/init.d/smb restart
3.7.8 配置复杂的共享
目标:实现共享的根下包含用户的各个组文件夹和用户私有文件夹
1)创建用户目录
In GlusterGW01 :
mkdir -p /data/share4
mkdir -p /data/share4/gp{1,2,s}
2)目录授权
In GlusterGW01 :
创建底层管理(排他)权限:
chown root:root /data/share4 chmod 700 /data/share4
允许特定的组访问读写执行
setfacl -m g:"CMDSCHOOL\gp1":rx /data/share4 setfacl -m g:"CMDSCHOOL\gp2":rx /data/share4
配置特定组文件夹访问权限
chown root:"CMDSCHOOL\gp1" /data/share4/gp1 chown root:"CMDSCHOOL\gp2" /data/share4/gp2 chown root:"CMDSCHOOL\gpS" /data/share4/gps chmod 770 /data/share4/gp*
配置特定组文件夹组权限自动继承
chmod g+s /data/share4/gp*
3)修改配置文件
In GlusterGW01 :
vim /data/samba.d/share4.smb.conf
加入如下配置:
[share4]
path = /data/share4
valid users = "@CMDSCHOOL\gps"
write list = "@CMDSCHOOL\gps"
create mask = 660
directory mask = 770
6)引入配置samba配置并使配置生效
In GlusterGW0{1-2} :
echo "include = /data/samba.d/share4.smb.conf" >> /etc/samba/smb.conf /etc/init.d/smb restart
3.7.9 增加windows的ACL支持
In GlusterGW0{1-2} :
[global] ... nt acl support = yes
注:以上配置完成用户可自行在windows下编辑文件的acl
3.7.10 文件类型过滤
1)创建类型库
In GlusterGW01 :
mkdir -p /data/samba.d/veto_files_type
2)创建视频规律规则
In GlusterGW01 :
vim /data/samba.d/veto_files_type/video.smb.conf
输入如下内容:
veto files = /*.264/*.3G2/*.3GP/*.3GP2/*.3GPP/*.3GPP2/*.3MM/*.3P2/*.60D/*.787/*.890/*.AAF/*.AEC/*.AEP/*.AEPX/*.AET/*.AETX/*.AJP/*.ALE/*.AM/*.AMC/*.AMV/*.AMX/*.ANIM/*.ANX/*.AQT/*.ARCUT/*.ARF/*.ASF/*.ASX/*.AVB/*.AVC/*.AVCHD/*.AVD/*.AVI/*.AVM/*.AVP/*.AVS/*.AVS/*.AVV/*.AWLIVE/*.AXM/*.AXV/*.BDM/*.BDMV/*.BDT2/*.BDT3/*.BIK/*.BIN/*.BIX/*.BMC/*.BMK/*.BNP/*.BOX/*.BS4/*.BSF/*.BU/*.BVR/*.BYU/*.CAMPROJ/*.CAMREC/*.CAMV/*.CED/*.CEL/*.CINE/*.CIP/*.CLK/*.CLPI/*.CMMP/*.CMMTPL/*.CMPROJ/*.CMREC/*.CMV/*.CPI/*.CPVC/*.CST/*.CVC/*.CX3/*.D2V/*.D3V/*.DASH/*.DAT/*.DAV/*.DB2/*.DCE/*.DCK/*.DCR/*.DCR/*.DDAT/*.DIF/*.DIR/*.DIVX/*.DLX/*.DMB/*.DMSD/*.DMSD3D/*.DMSM/*.DMSM3D/*.DMSS/*.DMX/*.DNC/*.DPA/*.DPG/*.DREAM/*.DSY/*.DV/*.DV-AVI/*.DV4/*.DVDMEDIA/*.DVR/*.DVR-MS/*.DVX/*.DXR/*.DZM/*.DZP/*.DZT/*.EDL/*.EVO/*.EVO/*.EXO/*.EYE/*.EYETV/*.EZT/*.F4F/*.F4P/*.F4V/*.FBR/*.FBR/*.FBZ/*.FCARCH/*.FCP/*.FCPROJECT/*.FFD/*.FFM/*.FLC/*.FLH/*.FLI/*.FLV/*.FLX/*.FPDX/*.FTC/*.G64/*.GCS/*.GFP/*.GIFV/*.GL/*.GOM/*.GRASP/*.GTS/*.GVI/*.GVP/*.GXF/*.H264/*.HDMOV/*.HDV/*.HKM/*.IFO/*.IMOVIELIBRARY/*.IMOVIEMOBILE/*.IMOVIEPROJ/*.IMOVIEPROJECT/*.INP/*.INT/*.IRCP/*.IRF/*.ISM/*.ISMC/*.ISMCLIP/*.ISMV/*.IVA/*.IVF/*.IVR/*.IVS/*.IZZ/*.IZZY/*.JMV/*.JSS/*.JTS/*.JTV/*.K3G/*.KDENLIVE/*.KMV/*.KTN/*.LREC/*.LRV/*.LSF/*.LSX/*.LVIX/*.M15/*.M1PG/*.M1V/*.M21/*.M21/*.M2A/*.M2P/*.M2T/*.M2TS/*.M2V/*.M4E/*.M4U/*.M4V/*.M75/*.MANI/*.META/*.MGV/*.MJ2/*.MJP/*.MJPEG/*.MJPG/*.MK3D/*.MKV/*.MMV/*.MNV/*.MOB/*.MOD/*.MODD/*.MOFF/*.MOI/*.MOOV/*.MOV/*.MOVIE/*.MP21/*.MP21/*.MP2V/*.MP4/*.MP4.INFOVID/*.MP4V/*.MPE/*.MPEG/*.MPEG1/*.MPEG2/*.MPEG4/*.MPF/*.MPG/*.MPG2/*.MPG4/*.MPGINDEX/*.MPL/*.MPL/*.MPLS/*.MPROJ/*.MPSUB/*.MPV/*.MPV2/*.MQV/*.MSDVD/*.MSE/*.MSH/*.MSWMM/*.MT2S/*.MTS/*.MTV/*.MVB/*.MVC/*.MVD/*.MVE/*.MVEX/*.MVP/*.MVP/*.MVY/*.MXF/*.MXV/*.MYS/*.NCOR/*.NSV/*.NTP/*.NUT/*.NUV/*.NVC/*.OGM/*.OGV/*.OGX/*.ORV/*.OSP/*.OTRKEY/*.PAC/*.PAR/*.PDS/*.PGI/*.PHOTOSHOW/*.PIV/*.PJS/*.PLAYLIST/*.PLPROJ/*.PMF/*.PMV/*.PNS/*.PPJ/*.PREL/*.PRO/*.PRO4DVD/*.PRO5DVD/*.PROQC/*.PRPROJ/*.PRTL/*.PSB/*.PSH/*.PSSD/*.PVA/*.PVR/*.PXV/*.QT/*.QTCH/*.QTINDEX/*.QTL/*.QTM/*.QTZ/*.R3D/*.RCD/*.RCPROJECT/*.RCREC/*.RCUT/*.RDB/*.REC/*.RM/*.RMD/*.RMD/*.RMP/*.RMS/*.RMV/*.RMVB/*.ROQ/*.RP/*.RSX/*.RTS/*.RTS/*.RUM/*.RV/*.RVID/*.RVL/*.SAN/*.SBK/*.SBT/*.SBZ/*.SCC/*.SCM/*.SCM/*.SCN/*.SCREENFLOW/*.SDV/*.SEC/*.SEC/*.SEDPRJ/*.SEQ/*.SFD/*.SFERA/*.SFVIDCAP/*.SIV/*.SMI/*.SMI/*.SMIL/*.SMK/*.SML/*.SMV/*.SNAGPROJ/*.SPL/*.SQZ/*.SRT/*.SSF/*.SSM/*.STL/*.STR/*.STX/*.SVI/*.SWF/*.SWI/*.SWT/*.TDA3MT/*.TDT/*.TDX/*.THEATER/*.THP/*.TID/*.TIVO/*.TIX/*.TOD/*.TP/*.TP0/*.TPD/*.TPR/*.TREC/*.TRP/*.TS/*.TSP/*.TTXT/*.TVLAYER/*.TVRECORDING/*.TVS/*.TVSHOW/*.USF/*.USM/*.VBC/*.VC1/*.VCPF/*.VCR/*.VCV/*.VDO/*.VDR/*.VDX/*.VEG/*.VEM/*.VEP/*.VF/*.VFT/*.VFW/*.VFZ/*.VGZ/*.VID/*.VIDEO/*.VIEWLET/*.VIV/*.VIVO/*.VIX/*.VLAB/*.VMLF/*.VMLT/*.VOB/*.VP3/*.VP6/*.VP7/*.VPJ/*.VRO/*.VS4/*.VSE/*.VSP/*.VTT/*.W32/*.WCP/*.WEBM/*.WFSP/*.WGI/*.WLMP/*.WM/*.WMD/*.WMMP/*.WMV/*.WMX/*.WOT/*.WP3/*.WPL/*.WSVE/*.WTV/*.WVE/*.WVX/*.WXP/*.XEJ/*.XEL/*.XESC/*.XFL/*.XLMV/*.XML/*.XMV/*.XVID/*.Y4M/*.YOG/*.YUV/*.ZEG/*.ZM1/*.ZM2/*.ZM3/*.ZMV/
3)创建音频规则
In GlusterGW01 :
vim /data/samba.d/veto_files_type/audio.smb.conf
输入如下内容:
veto files = /*.3GA/*.4MP/*.5XB/*.5XE/*.5XS/*.669/*.8SVX/*.A2B/*.A2I/*.A2M/*.A2P/*.A2T/*.A2W/*.AA/*.AA3/*.AAC/*.AAX/*.ABC/*.ABM/*.AC3/*.ACD/*.ACD-BAK/*.ACD-ZIP/*.ACM/*.ACT/*.ADG/*.ADT/*.ADTS/*.AFC/*.AGM/*.AGR/*.AHX/*.AIF/*.AIFC/*.AIFF/*.AIMPPL/*.AKP/*.ALAW/*.ALC/*.ALS/*.AMF/*.AMR/*.AMS/*.AMS/*.AMXD/*.AMZ/*.ANG/*.AOB/*.APE/*.APF/*.APL/*.ASD/*.AT3/*.AU/*.AU/*.AUD/*.AUP/*.AVASTSOUNDS/*.AXA/*.BAND/*.BAP/*.BDD/*.BIDULE/*.BMML/*.BNK/*.BRR/*.BUN/*.BWF/*.BWG/*.BWW/*.CAF/*.CAFF/*.CDA/*.CDDA/*.CDLX/*.CDO/*.CDR/*.CEL/*.CFA/*.CGRP/*.CIDB/*.CKB/*.CKF/*.CMF/*.CONFORM/*.COPY/*.CPR/*.CPT/*.CSH/*.CTS/*.CWB/*.CWP/*.CWS/*.CWT/*.DCF/*.DCM/*.DCT/*.DEWF/*.DF2/*.DFC/*.DFF/*.DIG/*.DIG/*.DJR/*.DLS/*.DM/*.DMC/*.DMF/*.DMSA/*.DMSE/*.DRA/*.DRG/*.DS2/*.DSF/*.DSM/*.DSS/*.DTM/*.DTS/*.DTSHD/*.DVF/*.DW/*.DWD/*.EFA/*.EFE/*.EFK/*.EFQ/*.EFS/*.EFV/*.EMD/*.EMP/*.EMX/*.EMY/*.EOP/*.ERB/*.ESPS/*.F2R/*.F32/*.F3R/*.F4A/*.F64/*.FAR/*.FDP/*.FEV/*.FLAC/*.FLM/*.FLP/*.FLP/*.FPA/*.FRG/*.FSB/*.FSC/*.FSM/*.FTI/*.FTM/*.FTM/*.FTMX/*.FUZ/*.FZF/*.FZV/*.G721/*.G723/*.G726/*.GBS/*.GIG/*.GMC/*.GP5/*.GPBANK/*.GPK/*.GPX/*.GROOVE/*.GSF/*.GSFLIB/*.GSM/*.GYM/*.H0/*.H3B/*.H3E/*.H4B/*.H4E/*.H5B/*.H5E/*.H5S/*.HBB/*.HBE/*.HBS/*.HDP/*.HMA/*.HPS/*.HSB/*.IAA/*.ICS/*.IFF/*.IGP/*.IMP/*.INS/*.INS/*.ISMA/*.IT/*.ITI/*.ITLS/*.JSPF/*.K26/*.KAR/*.KFN/*.KOZ/*.KOZ/*.KPL/*.KRZ/*.KSD/*.KSF/*.KT3/*.LA/*.LOGIC/*.LOGICX/*.LSO/*.LVP/*.LWV/*.M/*.M2/*.M3U/*.M3U8/*.M4A/*.M4B/*.M4P/*.M4R/*.MA1/*.MBR/*.MDC/*.MDR/*.MED/*.MGV/*.MID/*.MIDI/*.MINIGSF/*.MINIPSF/*.MINIPSF2/*.MINIUSF/*.MKA/*.MMF/*.MMLP/*.MMM/*.MMP/*.MMP/*.MMPZ/*.MO3/*.MOD/*.MOGG/*.MP2/*.MP3/*.MP_/*.MPA/*.MPC/*.MPDP/*.MPGA/*.MPU/*.MSCX/*.MSCZ/*.MSV/*.MTE/*.MTF/*.MTI/*.MTM/*.MTP/*.MTS/*.MU3/*.MUI/*.MUS/*.MUS/*.MUS/*.MUSX/*.MUX/*.MUX/*.MX3/*.MX4/*.MX5/*.MX5TEMPLATE/*.MXL/*.MXMF/*.MYR/*.NARRATIVE/*.NBS/*.NCW/*.NKB/*.NKC/*.NKI/*.NKM/*.NKS/*.NKX/*.NML/*.NMSV/*.NOTE/*.NRA/*.NRT/*.NSA/*.NST/*.NTN/*.NWC/*.OBW/*.ODM/*.OGA/*.OGG/*.OKT/*.OMA/*.OMF/*.OMG/*.OMX/*.OPUS/*.OTS/*.OVE/*.OVW/*.PANDORA/*.PCA/*.PCAST/*.PCG/*.PCM/*.PEAK/*.PEK/*.PJUNOXL/*.PK/*.PKF/*.PLA/*.PLS/*.PLST/*.PLY/*.PNA/*.PPC/*.PSF/*.PSF1/*.PSF2/*.PSM/*.PTCOP/*.PTF/*.PTM/*.PTS/*.PTT/*.PTX/*.PTXT/*.PVC/*.Q1/*.Q2/*.QCP/*.R1M/*.RA/*.RAD/*.RAM/*.RAX/*.RBS/*.REX/*.RFL/*.RGRP/*.RIP/*.RMI/*.RMJ/*.RMX/*.RNG/*.RNS/*.ROL/*.RSF/*.RSN/*.RSO/*.RTA/*.RTI/*.RX2/*.S3I/*.S3M/*.SAF/*.SAP/*.SBG/*.SBI/*.SC2/*.SCS11/*.SD/*.SD/*.SD2/*.SDAT/*.SDS/*.SEQ/*.SES/*.SESX/*.SF2/*.SFK/*.SFL/*.SFPACK/*.SFZ/*.SGP/*.SHN/*.SIB/*.SLP/*.SLX/*.SMA/*.SMF/*.SMP/*.SMP/*.SMPX/*.SND/*.SND/*.SNG/*.SNG/*.SNS/*.SOU/*.SPH/*.SPPACK/*.SPRG/*.SSEQ/*.SSEQ/*.SSM/*.SSND/*.STAP/*.STM/*.STX/*.STY/*.SVD/*.SVQ/*.SVX/*.SWA/*.SXT/*.SYH/*.SYN/*.SYW/*.SYX/*.TAK/*.TD0/*.TG/*.THX/*.TOC/*.TRAK/*.TSP/*.TTA/*.TXW/*.U/*.UAX/*.UB/*.ULT/*.UNI/*.USF/*.USFLIB/*.UST/*.UW/*.UWF/*.V2M/*.VAG/*.VAP/*.VC3/*.VCE/*.VIP/*.VLC/*.VMD/*.VMF/*.VMO/*.VOC/*.VOX/*.VOXAL/*.VPL/*.VPM/*.VPW/*.VQF/*.VRF/*.VSQ/*.VSQX/*.VTX/*.VYF/*.W01/*.W64/*.WAV/*.WAV/*.WAVE/*.WAX/*.WEM/*.WFB/*.WFD/*.WFM/*.WFP/*.WMA/*.WOW/*.WPK/*.WPP/*.WPROJ/*.WRK/*.WUS/*.WUT/*.WV/*.WVC/*.WVE/*.WWU/*.XA/*.XA/*.XBMML/*.XFS/*.XM/*.XMI/*.XMS/*.XMU/*.XPF/*.XRNS/*.XSP/*.XSPF/*.YOOKOO/*.ZGR/*.ZPL/*.ZVD/
4)导入过滤规则
In GlusterGW0{1-2} :
vim /etc/samba/smb.conf
修改配置如下:
[global] ... include = /data/samba.d/veto_files_type/video.smb.conf include = /data/samba.d/veto_files_type/audio.smb.conf
重启服务是配置生效
/etc/init.d/smb restart
5)其他文类型请参阅
http://fileinfo.com/browse/
—————————————————————-
参阅文档
—————————————————————-
官方文档
———-
用户文档:
https://wiki.samba.org/index.php/Main_Page
企业samba的安装包:
https://samba.plus/older-packages/
https://samba.plus/samba-3/red-hats-rhel/
http://ftp.sernet.de/pub/samba/3.4/rhel/6/x86_64/
Samba+的源
https://portal.enterprisesamba.com/
官方配置文档:
https://wiki.samba.org/index.php/User_Documentation
配置samba成为域成员:
https://wiki.samba.org/index.php/Setup_Samba_as_an_AD_Domain_Member
https://www.samba.org/samba/docs/man/Samba-Guide/unixclients.html
配置一个sambaAD域控制器:
https://wiki.samba.org/index.php/Setup_a_Samba_Active_Directory_Domain_Controller
加一个额外的DC到现有的活动目录:
https://wiki.samba.org/index.php/Join_an_additional_Samba_DC_to_an_existing_Active_Directory
本地samba数据库信息:
https://wiki.samba.org/index.php/Frequently_Asked_Questions
winbind的离线登录
https://wiki.samba.org/index.php/PAM_Offline_Authentication
———–
非官方文档
———–
理论文章:
http://www.tuicool.com/articles/ie6fue
samba的搭建:
http://www.toxingwang.com/linux-unix/linux-admin/584.html
http://wenku.baidu.com/link?url=l740EpqsM_JxQh0U7IjlCtZ07IPs-0bBBK7UO7D6O_sfVi4Ps8DnZ5UzejGTETTENlXzjSjMAC0DmvNH1P0Gy2CvGGxCJO907V2zGYMAyfa
samba的权限控制:
http://os.51cto.com/art/201101/243960.htm
AD用户数量统计:
http://jankie.blog.51cto.com/6640/104269
——–
samba 集群
———–
https://wiki.samba.org/index.php/Clustered_Samba
http://www.tuicool.com/articles/rYJBZb
https://wiki.samba.org/index.php/CTDB_Setup#Critical_smb.conf_parameters
kerberos
http://blog.csdn.net/wulantian/article/details/42418231
http://www.cnblogs.com/artech/archive/2011/01/24/kerberos.html
http://blog.sina.com.cn/s/blog_716c1cc8010119ne.html
http://blog.scottlowe.org/2007/07/09/uac-and-ktpassexe/
http://www.tuicool.com/articles/ie6fue
常见的Krb5错误消息:
http://joshuasabrina.iteye.com/blog/1895281
IBM的文章
http://www.ibm.com/developerworks/cn/linux/l-lpic3-313-3/
smb.conf的配置
https://www.samba.org/samba/docs/man/manpages-3/smb.conf.5.html
SSSD
https://fedorahosted.org/sssd/
https://fedorahosted.org/sssd/wiki/Configuring_sssd_with_ad_server
SETSPN.exe命令的用法
http://blog.csdn.net/wzhwho/article/details/6169624
Windows SID的修改
http://www.youranshare.com/push/topics/softuse/502.html
